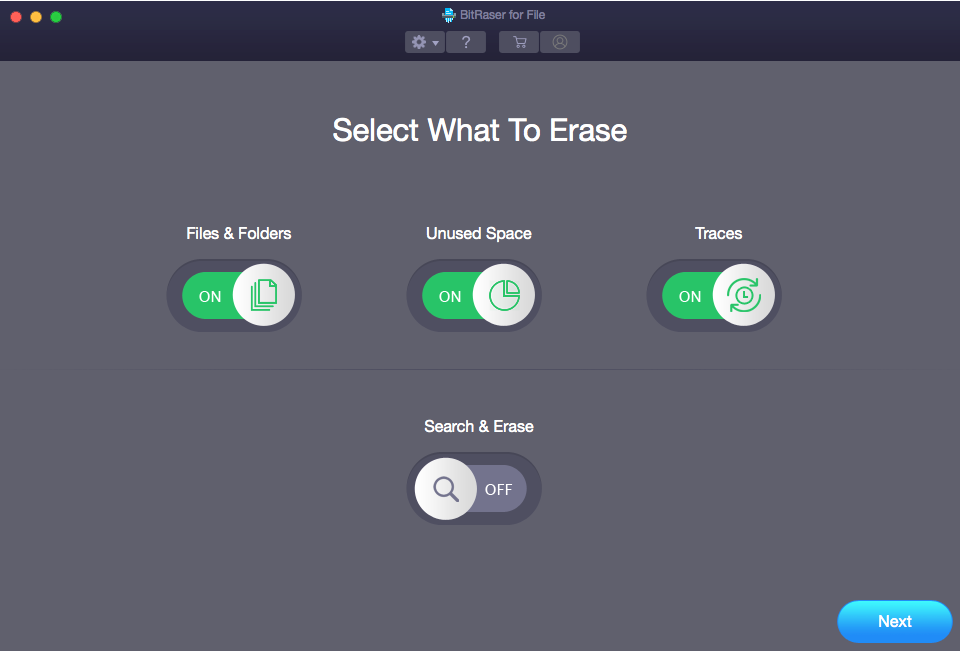
Review: BitRaser File Eraser (Mac)
The question of how to erase data on Mac or any other platform might seem like a relatively simple one,…
Technology News from the World's Most Influential Companies

The question of how to erase data on Mac or any other platform might seem like a relatively simple one,…
![Do Americans Understand Basic Internet Safety? [Infographic] internet security](https://1reddrop.com/wp-content/uploads/2018/12/internet-security.jpg)
Believe it or not, large corporations and billionaires aren’t the only entities susceptible to cyber attacks. Last year, nearly 17…

Data recovery is a complex task that is not easily accomplished without the right tools at your disposal. Much of…

Spring is the time to clean out those attics, beat those carpets and prepare your home for a new season…

We’ve done quite a few software reviews on 1redDrop, and one of the things we’ve noticed in the past year…

Imagine you’re working on a great project and all of a sudden your screen goes blank, an indication of a…

Cybercrime. The word is enough to send a chill down anyone’s spine these days. And that includes the 300 million…
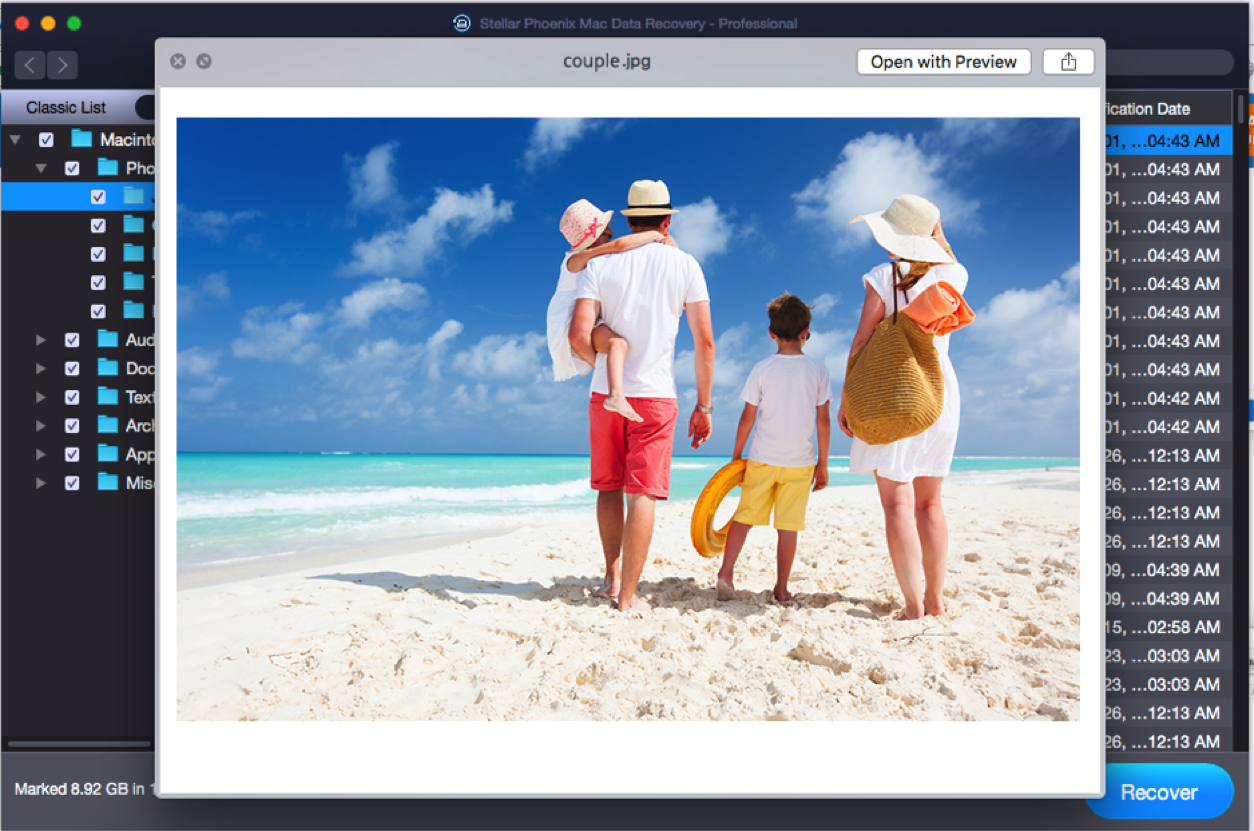
When I lost some important files in the documents folder while doing a macOS High Sierra upgrade recently, I used…

When you have several accounts that are password-protected or you are the kind of person who can’t remember passwords, it…

Nearly 123 million households had their personal information exposed in a fiasco involving an improperly configured AWS storage bucket by…

Data recovery is often an undervalued component of data security. Most individual users are not even aware of the many…

Why would a defense contractor be allowed to handle sensitive information when their network isn’t highly secure? That’s the question…
If you thought you could delete all your history with Google from your Chrome settings, you’re only partially right. Google…

Data is one of the most valuable assets today whether you’re an individual, a small business or a large corporation….
Google today launched a much-anticipated desktop app called Backup and Sync. Not one to mince words, the company is encouraging…