The iOS malware known as Pegasus has now struck the Android system as a variant on the original. What makes this variant even more dangerous than the original iOS version? And what is the extent of damage it can do to Android devices? More importantly, what is the current threat level to Android device users?
What is the Malware Known as Pegasus all About?
Developed by Israel-based NSO Group, Pegasus was originally developed for both iOS and Android operating systems. The company made its name selling software for government surveillance. The first detected attack on iOS was in the UAE, against human rights activist Ahmed Mansoor, who immediately informed security researchers at Citizens Labs, which then collaborated with Lookout to investigate the malware.
How Does Pegasus Work on iOS Devices?
On iOS devices, Pegasus starts with a simple text message that used three zero-day vulnerabilities to compromise the device. Once in, the malware spares nothing, compromising nearly every app on the phone from iMessage to Gmail to Facebook and even passwords.
Why is the Android Variant of Pegasus Even More Dangerous?
The Android version is far more devious because it does not require zero-day vulnerabilities to mount an attack. It can still compromise the device in the same way as an iOS device, in the process keylogging, capturing screenshots and being able to be controlled remotely via SMS. Here’s a full list as provided by Lookout:
- Keylogging
- Screenshot capture
- Live audio capture
- Remote control of the malware via SMS
- Messaging data exfiltration from common applications including WhatsApp, Skype, Facebook, Twitter, Viber, Kakao
- Browser history exfiltration
- Email exfiltration from Android’s Native Email client
- Contacts and text message
The really scary part is that it has the ability to self-destruct if a kill command is issued or if the malware senses the risk of detection. As explained by Lookout:
“Pegasus for Android does not require zero-day vulnerabilities to root the target device and install the malware. Instead, the threat uses an otherwise well-known rooting technique called Framaroot.
“In the case of Pegasus for iOS, if the zero-day attack execution failed to jailbreak the device, the attack sequence failed overall. In the Android version, however, the attackers built in functionality that would allow Pegasus for Android to still ask for permissions that would then allow it to access and exfiltrate data. The failsafe jumps into action if the initial attempt to root the device fails.”
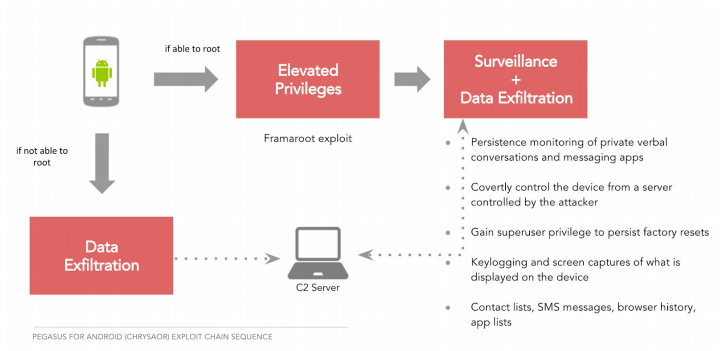
Google has renamed the Android variant of Pegasus “Chrysaor”, but is placating users:
“It is extremely unlikely you or someone you know was affected by Chrysaor malware.
“Through our investigation, we identified less than 3 dozen devices affected by Chrysaor, we have disabled Chrysaor on those devices, and we have notified users of all known affected devices. Additionally, the improvements we made to our protections have been enabled for all users of our security services.”
This is exactly the type of scenario that plays out on a regular basis in the world of cybersecurity. The bad actors stay one step ahead of the good guys, and the key element is to bring down the time taken to identify and apply remediation.
ALSO READ: Google Educates Android Users on Security Features for Ransomware Attacks
This time, Android users were lucky that only a very small number of devices were affected, thanks to the vigilance of Lookout and quick action by the Google Security team.
A full report for Pegasus/Chrysaor by Lookout can be found here.
Thanks for reading our work! If you enjoyed it or found value, please share it using the social media share buttons on this page. If you have something to tell us, there’s a comments section right below, or you can contact@1redDrop.com us.



