A new macOS malware program has been discovered in Europe, and it is being spread via phishing emails. Security researchers at Check Point Software Technologies are calling it OSX/Dok, and the payload is delivered via an email attachment.
One of these emails was analyzed by the team at Check Point, and was built to look like a notification from a Swiss government agency warning the recipient about errors in their tax returns. A zipped file called Dokument.zip was attached to the email, and contained the malware payload.
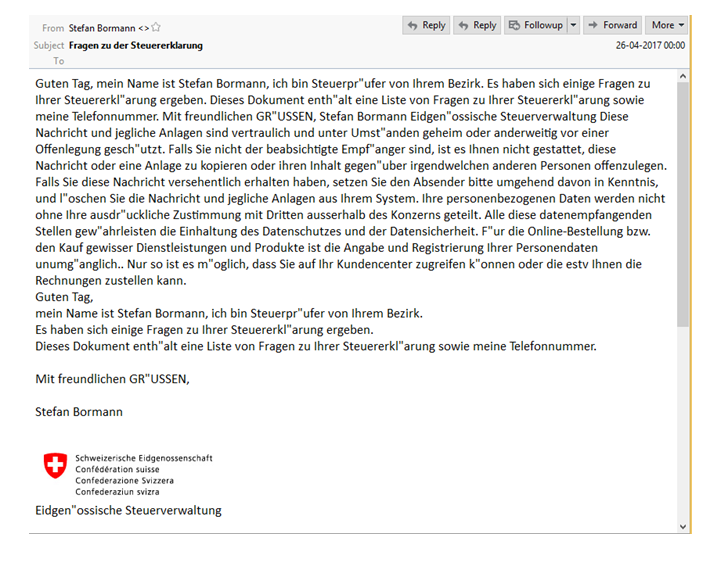
Interestingly, the malware is actually digitally signed with a valid Apple developer certificate. It’s not clear at this point whether the hackers set up a fake ID to join the Apple Developer Program or whether the certificate was stolen from a genuine developer account. The certificate in question is issued by Apple to third-party developers, and allows them the right to publish apps on the the Mac App Store.
What does the OSX/Dok Malware Do on macOS Machines?
Essentially, once you click on the file and download it, it unzips and pushes a fake notification about having to install a system security update. Users who unknowingly agree to install it will be asked for their admin password, as is the case with any update or software installation on a macOS machine.
Once OSX/Dok gets the admin privileges, it will automatically make the active user (you) a permanent administrator so you won’t get any other prompts while the malware is executing admin-level commands without your knowledge.
The clever malware program then takes over your web traffic, re-directing it to a proxy server that is controlled by the hackers.
It’s even more devious than you think because that server is located on a Tor network that is provided a high level of anonymity, making it almost impossible to track the hackers down. The malware does this by installing a Tor client on your system and starting it up automatically. You won’t know this because you’ve already been made a permanent administrator, with the highest level of privileges.
The proxy server part is required so the hackers can decrypt the web traffic coming and going from your macOS system, and perform what’s called a Man in the Middle attack, or MitM, for short. This decrypt and re-encrypt process works on HTTPS connections that are usually used for sensitive transactions like account logins, online banking and so on, which is what makes this malware extremely dangerous to the user.
By using a rogue root certificate, the attackers fool the system into thinking that there’s nothing going on in the background, when there actually is.
Check Point researchers have contacted Apple and have worked with them to mitigate this particular phishing campaign, but they remain vigilant, looking for similar attack campaigns or variants of the OSX/Dok malware.
One last point to think about:
Just because this happened in Europe, it doesn’t mean that people elsewhere, like the United States, for example, are safe from such an attack. There may be variants on the loose in the wild, or versions created for specific countries (since the phishing method was related to tax returns.)
The occurrence of tax-related malware usually increases dramatically during important income tax-related dates around the world.
The best way to prevent a phishing attack via email is to disregard and/or delete all suspicious-looking emails, no matter how genuine they might seem. Hackers are getting smarter by the day, and all it takes is a little more time and effort to create emails, pop-up notifications and other alerts to make you think what you are seeing is legitimate.
Be safe. Don’t download attachments without scanning them first. If you think something is fishy, contact the authority that the email is purported to be from to sort it out. User caution is usually the best security measure.
Thanks for visiting! Would you do us a favor? If you think it’s worth a few seconds, please like our Facebook page and follow us on Twitter. It would mean a lot to us. Thank you.



