Google Chrome is the dominant browser on the desktop and mobile environments, covering billions upon billions of devices around the world. Soon after the major cyber threat posed to users from the Google Chrome vulnerability that allowed phishing attacks to go undetected, a new report has emerged from Android security researcher Rowland Yu of SophosLabs.
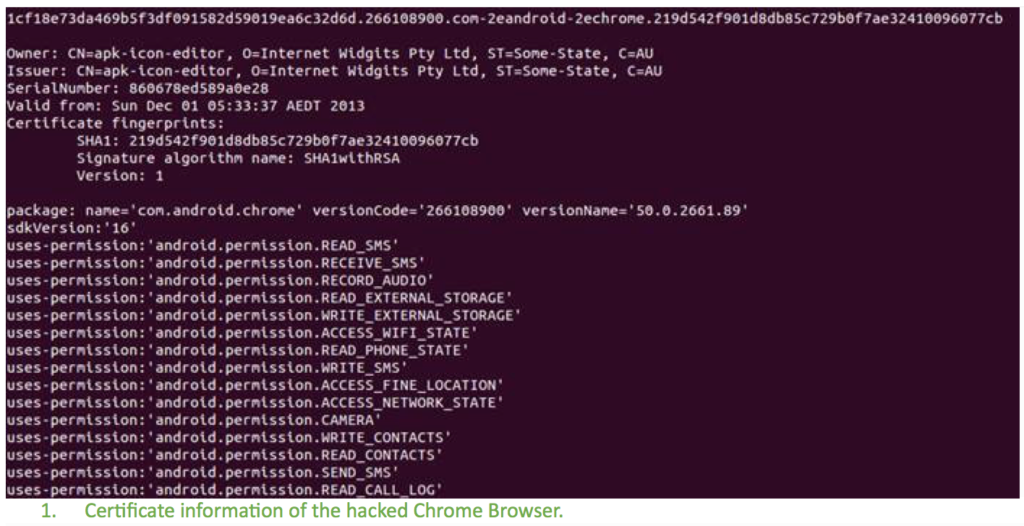
According to a blog post by Sophos, the newly detected malware, called Andr/SandRat-C, was found in a hacked version of Google Chrome for Android, and is “built to evade the digital signatures at the heart of modern security procedures.”
Thankfully, this particular version of the hacked Google Chrome app for Android devices is not on Google Play Store, but another piece of malware with the same kind of functionality is on the app store.
According to Bill Brenner of Sophos:
The main point is that Google Play allows a compromised certificate , though they know the certificate has been used to sign rootkit malware.
But it doesn’t end here. There are roughly 1,000 apps outside the Google Play Store that Android users regularly install on their devices using the APK method.
Once the payload is delivered, the malware in question proceeds to access various functions on the device, such as recording audio, taking photos and videos, listening in on your calls, sending SMSes, sending SMS content, querying the phone’s location and so on.
The problem here is with the certificate itself, which appears to have been compromised. The same certificate has reportedly been used to sign a different rootkit – Andr/Rootnik-AH. That rootkit was on Google Play until recently, when it was removed, shows the report.
Digital certificates are central to the security landscape. As Yu explains:
“In Android, all APKs are required to be digitally signed with a certificate before they can be published and installed. A digital signature consists of a public/private key pair. An APK signed with a developer’s private key can be verified by anyone who can access the public key inside the APK. The developer has the responsibility of maintaining the security of the private key.”
If a particular digital certificate has been compromised, it can be used to sign an app containing any kind of malware. In the case of the hacked Google Chrome, it will bypass all of the safeguards built into your Android device because it is a legitimate certificate.
The good news is, if you’re updating Google Chrome directly from Play Store, you’re safe because the hacked version isn’t allowed there. On the other hand, if you’re downloading an APK from an unknown source and installing it that way, that could put your device at serious risk.
The Perils of Sideloading Apps using the APK Method
Unfortunately, sideloading an app on an Android device using the APK method is so simple that a lot of people do it regularly without realizing the threat to their data or their device.
If you must use the APK method, be sure to use one of the trusted sites that provide APKs, such as APKMirror. Sites like this are generally safer than most, though not entirely foolproof. What they do is check the certificate on the APK version against other builds of the same application, to make sure they match.
For example, if this hacked Google Chrome version had gone through their checkpoints, it would likely have been caught out because it isn’t signed with the same digital certificate that other Google Chrome versions are.
If you’re an incorrigible sideloader, good for you. But be careful what you’re sideloading on your Android device. Hopefully, it’s not the hacked version of Google Chrome for Android.
Thanks for visiting! Would you do us a favor? If you think it’s worth a few seconds, please like our Facebook page and follow us on Twitter. It would mean a lot to us. Thank you.



