
Keeping Your Data Secure 100% Of The Time With VoIP: 5 Things To Implement Right Away
Have you finally ditched landlines for the better and more advanced VoIP? If so, great! There’s so much more than…
Technology News from the World's Most Influential Companies

Have you finally ditched landlines for the better and more advanced VoIP? If so, great! There’s so much more than…

Catfishing is a dangerous game. You never know who you’re really talking to online, and it’s easy to get caught…

Business owners and managers often pass off any measures towards cybersecurity thinking that no hacker would ever trouble them. Malware…

Internet users use VPNs because they want to surf without third parties eavesdropping. It is a relief for most people…
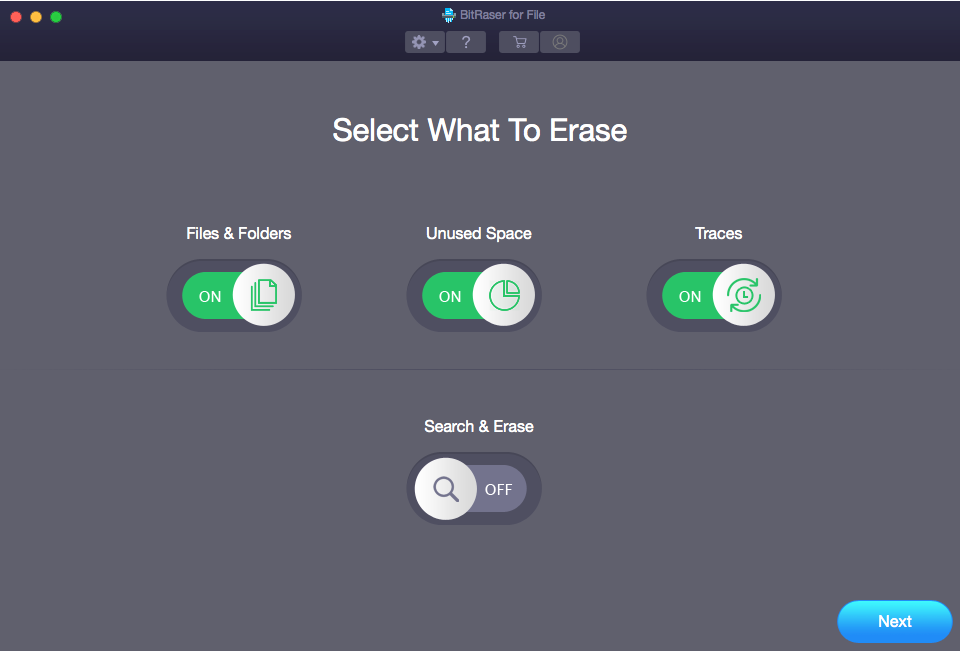
The question of how to erase data on Mac or any other platform might seem like a relatively simple one,…

If you’re a responsible homeowner, we’d be willing to bet that you put a major emphasis on your home security….

Most businesses today use cyber technology to retain, access and utilize data. With this in mind, companies should be savvier…
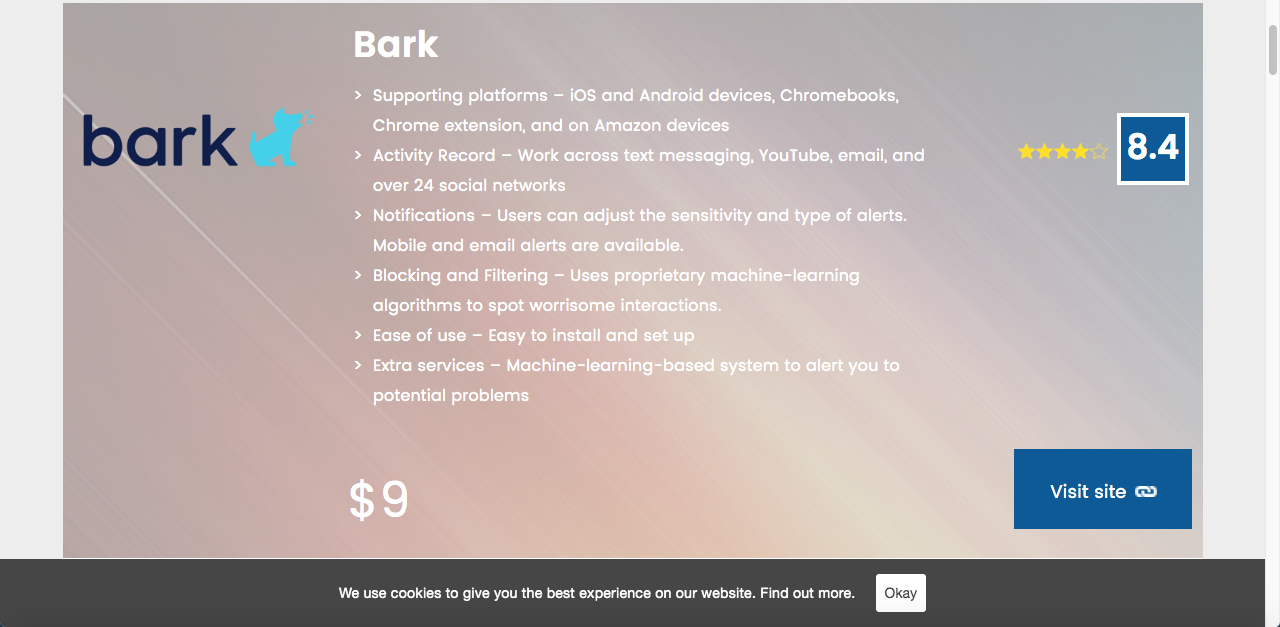
Instagram is considered the worst social media and even dubbed as a gateway for child abuse. With this, it makes…

Life is a very precious gift given to us by God for which I believe that we can never repay…

Many organizations are not in the technology business, and the work of hosting their own infrastructure can be a distraction…

Worried that your spouse might be cheating on you? Catch cheaters texting their secret lovers with this intriguing spy app…

Your online presence can be a great means of making good money and a platform to interact with people from…

The internet has gone global, and we all know that the system may have many technologies and other tools or…

Phishing scams have become quite a real problem in the past few years and there is no sign they will…
![Your Cheat Sheet for Cybersecurity [Infographic]: Most Expensive Data Breaches and More cybersecurity infographic](https://1reddrop.com/wp-content/uploads/2019/03/cybersecinfo.jpeg)
What do you know about cybersecurity? If you’re like most people, you know that you need to have an antivirus…